30 Days of MLOps Challenge · Day 16
 Security in MLOps – Protecting ML Systems at Every Layer
Security in MLOps – Protecting ML Systems at Every Layer
Safeguard ML systems from threats like data poisoning, model theft, and adversarial attacks. Secure every layer—from data pipelines to model deployment—for reliability, compliance, and trust.
Key Learnings
- Understand the security risks unique to ML systems (data poisoning, model theft, adversarial attacks)
- Learn about model access control, authentication, and authorization
- Implement API security practices such as rate limiting, input validation, and logging
- Gain awareness of adversarial machine learning threats
- Explore how to secure training data, pipelines, model artifacts, and serving endpoints
Learn here
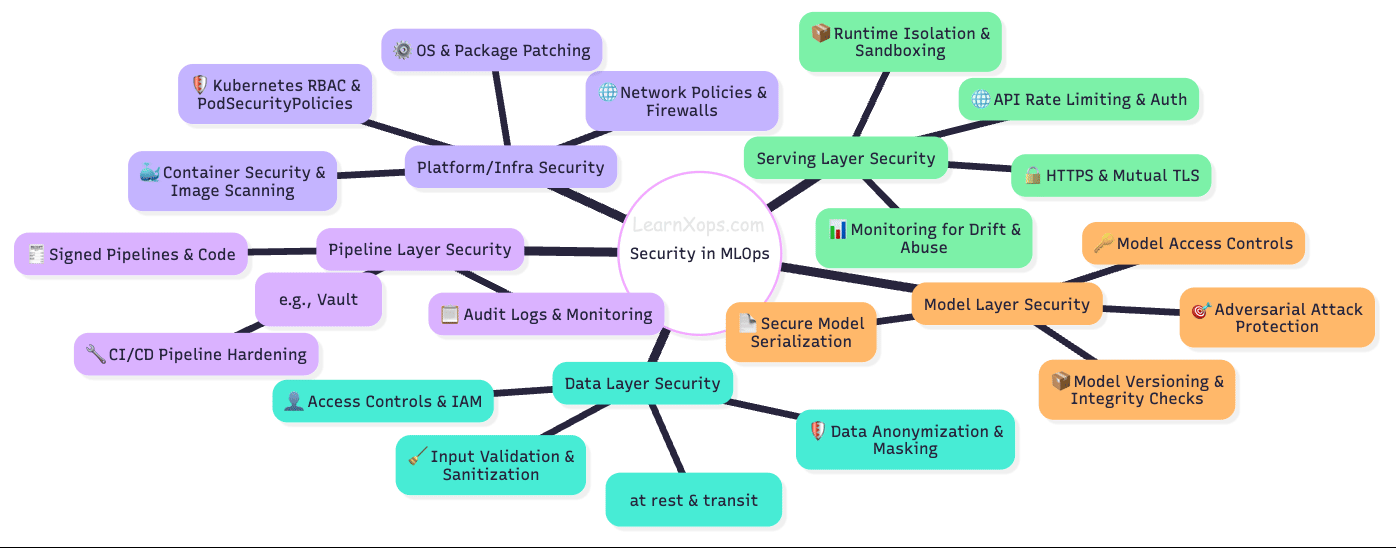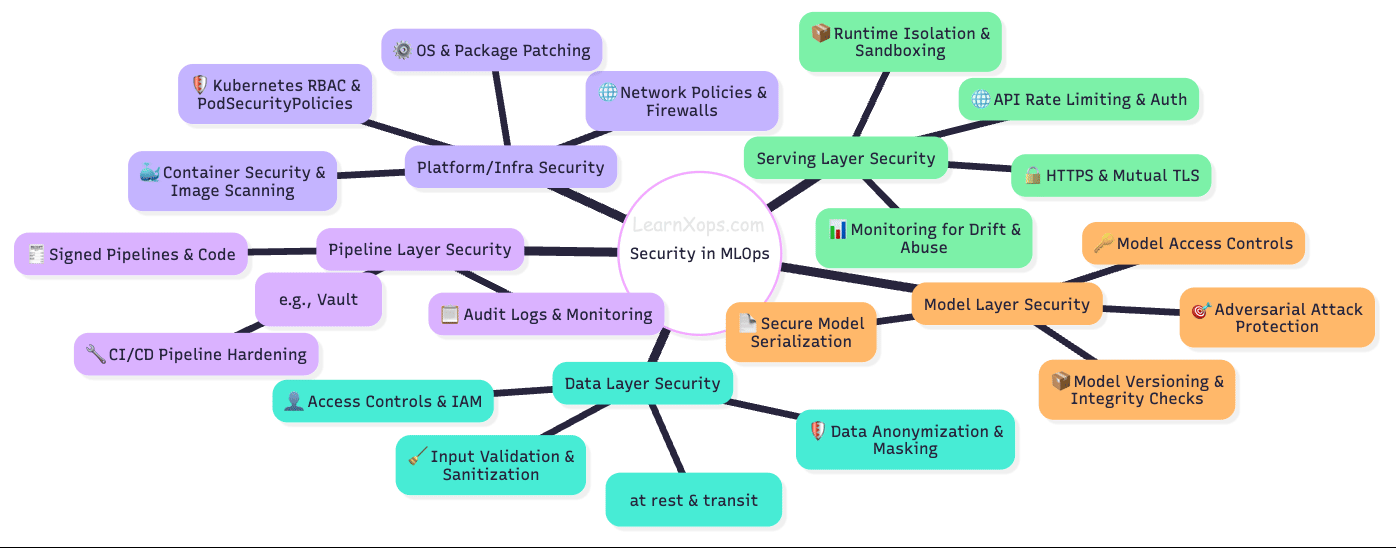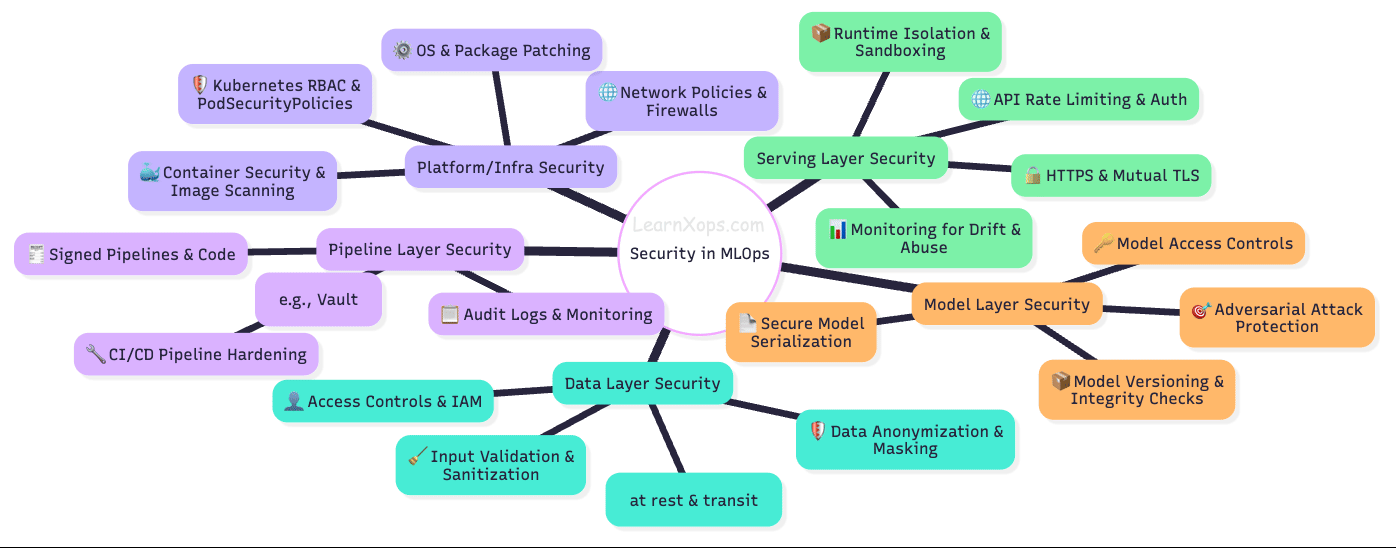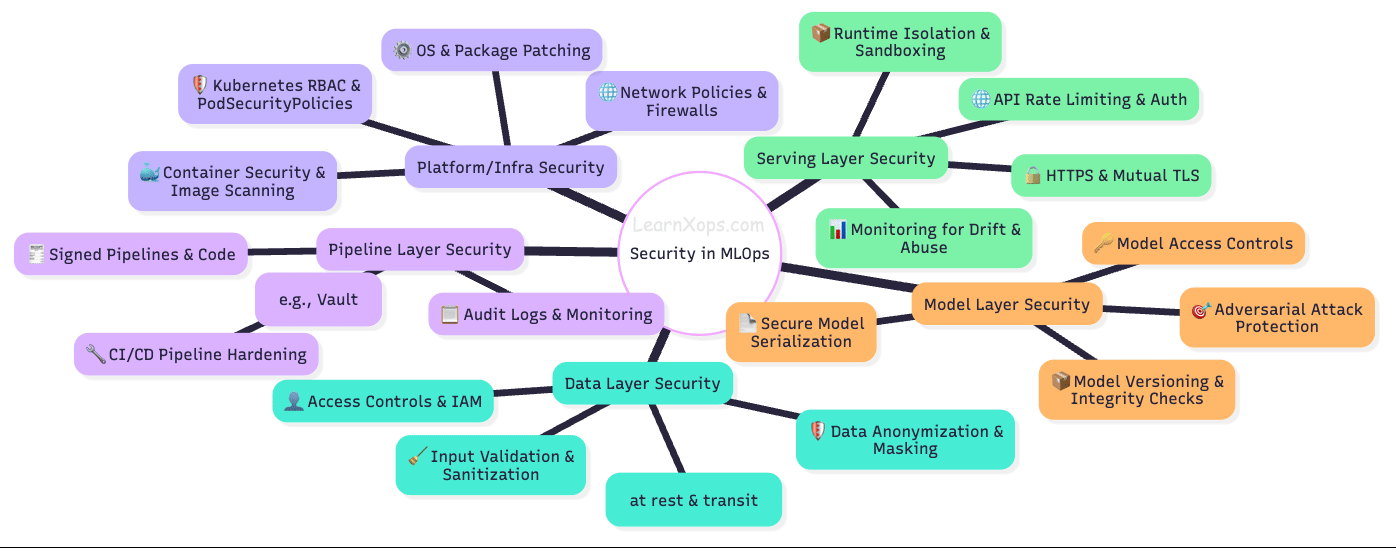
Security in MLOps
Security in MLOps refers to implementing security best practices across the entire machine learning lifecycle — from data ingestion to model deployment and monitoring — to ensure the integrity, confidentiality, and availability of ML systems.
Key Areas of Security in MLOps:
- Data Security: Secure data storage and access, encryption, lineage, auditability, and prevention of data poisoning.
- Model Security: Protect models from theft, secure model artifacts, use encryption, and secure APIs.
- Pipeline & Infrastructure Security: Secure CI/CD, secrets management, container security, RBAC.
- Adversarial ML Protection: Defend against adversarial inputs, validate inputs, monitor inference.
- API Security: Authentication, rate limiting, input validation, logging.
- Governance & Compliance: Explainability, traceability, regulatory compliance, audit trails.
- Monitoring & Incident Response: Detect anomalous predictions, set up alerting and logging.
Security Deep Dive: Risks in Machine Learning Systems
Unique Risks
- Data Poisoning: Malicious data inserted into training to influence model behavior.
- Model Theft: Attackers reconstruct or steal deployed models via queries.
- Adversarial Attacks: Crafted inputs fool models into wrong predictions.
Mitigation Strategies
- Data validation and sanitization
- Robust learning algorithms
- API rate limiting and monitoring
- Adversarial training and input sanitization
- Access control and authorization
Model Access Control, Authentication, and Authorization
- Authentication: API Keys, OAuth2, JWT, mTLS
- Authorization: RBAC, ABAC, policy-based access
- Model registry-level access control
- Audit and monitor all access
Best Practices
- Rotate credentials and tokens regularly
- Use least privilege principle
- Encrypt sensitive data
- Periodic security reviews
API Security Best Practices
- Rate limiting (e.g., NGINX, API Gateway)
- Input validation (OpenAPI, pydantic, Joi)
- Logging and monitoring (ELK, Prometheus, Grafana)
- HTTPS, authentication, CORS, WAF
Adversarial Machine Learning Threats
- Evasion, poisoning, model inversion, membership inference, model stealing
- Defense: adversarial training, input sanitization, monitoring, ensemble methods
Tools
- CleverHans, Foolbox, ART, TensorFlow Privacy
Securing Training Data, Pipelines, Model Artifacts, and Serving Endpoints
- Access control, encryption, data versioning, anonymization, auditing
- Pipeline authentication, code signing, secrets management, audit logs
- Artifact integrity, storage security, encryption
- Endpoint authentication, rate limiting, input validation, monitoring
Tooling Overview
| Security Area | Tool Suggestions |
|---|---|
| Data Access & Audit | AWS IAM, GCP IAM, Azure AD, LakeFS |
| Pipeline Security | Kubeflow Pipelines, TFX, Argo Workflows, OPA |
| Artifact Security | MLflow, S3 Versioning, Hashing tools, Sigstore |
| Endpoint Security | Istio, Kong, API Gateway, Falco, Prometheus + Grafana |
🔥 Challenges
- Secure your ML model endpoint with API key or token-based access
- Adversarial testing with Foolbox or ART
- Sign model files and verify at runtime
- Scan Docker containers for vulnerabilities
- Configure IAM or Kubernetes RBAC for pipelines and artifacts
- Implement audit logs for model inferences
- Store models in secure registries
- Rate limiting and logging for APIs